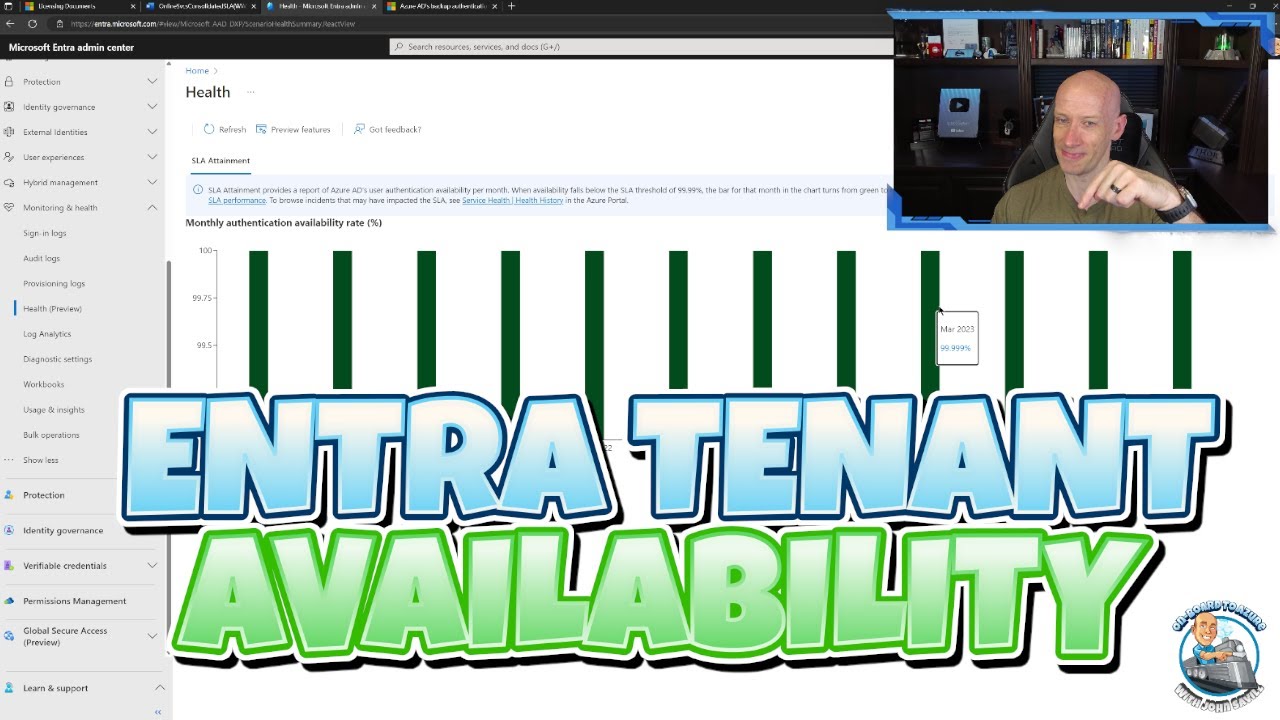
Viewing your Microsoft Entra (Azure AD) Tenant Authentication Availability
How to check your tenant's historical authentication availability.
- Introduction to Microsoft Entra tenant authentication availability.
- The official SLA refers to the Service Level Agreement between the service provider and the customer
- Checking your tenant's availability will provide assurance that the tenant and its resources are accessible and functional.
- The term 'backup authentication' is used to refer to the secondary method of confirming the tenant's identity.
- Checking whether backup authentication has been used lets you understand the system resilience in case of primary method failure.
Key links include:
- Normal SLA document: SLA Document.
- Backup Authentication: Backup Authentication System.
Azure AD's Backup Authentication System
Azure Active Directory (Azure AD) ensures a 99.99% service level availability for user and service authentication. The resilience of this authentication service is further improved by a backup system that was implemented in 2021.

Overview
The Azure AD backup authentication system consists of multiple backup services that work together to increase authentication resilience during an outage. If the primary Azure AD service is unavailable or degraded, this system transparently and automatically handles authentications for supported applications and services, thereby adding an extra layer of resilience. The system syncs authentication metadata when it's healthy, enabling users to continue accessing applications during outages of the primary service while enforcing policy controls.
Application Support
Users can continue working with their applications during an outage if they accessed them in the last three days from the same device, and no blocking policies exist that would curtail their access.
Supported applications include:
- Microsoft applications
- Native email clients on iOS and Android
- SaaS applications available in the app gallery
- Selected line of business applications, based on their authentication patterns
- Service to service authentication that relies on Azure AD managed identities or built on Azure services
Non-Microsoft Workloads
The backup authentication system provides incremental resilience to supported non-Microsoft applications based on their authentication patterns. Supported non-Microsoft apps include native applications using the OAuth 2.0 protocol, line of business web applications configured to authenticate with OpenID Connect using only ID tokens, and web applications authenticating with the SAML protocol when configured for IDP-Initiated Single Sign On (SSO).
However, certain authentication patterns are not supported such as web applications that authenticate using Open ID Connect and request access tokens, and web applications that use the SAML protocol for authentication, when configured as SP-Initiated SSO.
User Support Conditions
During an outage, a user can authenticate using the backup authentication system if:
- The user has successfully authenticated using the same app and device in the last three days
- The user isn't required to authenticate interactively
- The user is accessing a resource as a member of their home tenant, not in a B2B or B2C scenario
- The user isn't subject to Conditional Access policies that limit the backup authentication system
- The user hasn't been subject to a revocation event, such as a credential change since their last successful authentication
Interactive Authentication and User Activity
The backup authentication system relies on metadata from a prior authentication to reauthenticate the user during an outage. Therefore, a user must have authenticated in the last three days using the same app on the same device for the backup service to be effective.
Conditional Access Policies
Certain policies can't be evaluated in real-time by the backup authentication system and must rely on prior evaluations. Tenant administrators can choose a strict evaluation of all Conditional Access policies by disabling resilience defaults but this decision should be taken with care because it disables those users from using backup authentication.
Workload Identity Resilience
The backup authentication system provides resilience for managed identities and other key Azure infrastructure by offering a regionally isolated authentication service. Your services built on the Azure Infrastructure using managed identities and Azure services authenticating with each other are protected by the backup authentication system. However, your services built on or off Azure when the identities are registered as Service Principals and not “managed identities” aren't protected by the backup authentication system.
Deep-Dive into Microsoft Entra (Azure AD) Tenant Authentication Availability
This focuses on the significance of keeping track of your tenant's historical authentication availability. Understanding your tenant's availability allows to monitor your resources and ensures that they are functioning as expected. The backup authentication method offers an additional layer of protection and security for your data, thus enabling you to maintain consistent operations. Furthermore, this process aids customers to have a clear understanding of the terms outlined in the SLA.
Learn about Viewing your Microsoft Entra (Azure AD) Tenant Authentication Availability
Microsoft Entra (Azure AD) is an authentication service that helps customers to securely access their applications and resources. In this tutorial, we will explore how to view your tenant's authentication availability and what the official Service Level Agreement (SLA) is. We will also look at how to check if your tenant's authentication is available, what uses backup authentication, and if backup authentication has been used.
The official SLA states that the service guarantees a 99.9% availability. This means that customers can expect the service to be available 99.9% of the time. To check your tenant's availability, you can use the Azure portal to view the historical authentication availability data.
Backup authentication is used when the primary authentication fails. This could be due to a number of reasons, including network outages or user-related issues. To find out if backup authentication has been used, you can check the backup authentication status.
In summary, this tutorial has discussed how to view your tenant's authentication availability. We looked at the official Service Level Agreement (SLA) and how to check if your tenant's authentication is available. We also discussed what uses backup authentication and how to check if backup authentication has been used.

More links on about Viewing your Microsoft Entra (Azure AD) Tenant Authentication Availability
- Azure Active Directory feature availability
- Apr 13, 2023 — Learn which Azure AD features are available in Azure Government. ... Federated authentication (Active Directory Federation Services or ...
- Quickstart: View enterprise applications - Azure
- Jun 14, 2023 — View the enterprise applications that are registered to use your Azure Active Directory tenant.
- Azure AD Pass-through Authentication - Quickstart
- May 4, 2023 — Sign in to the Entra admin center with the Hybrid Identity Administrator credentials for your tenant. · Select Azure Active Directory. · Select ...
- Pass-through Authentication - Upgrade auth agents - ...
- Step 2: Check the versions of your Authentication Agents · Go to Control Panel -> Programs -> Programs and Features on the on-premises server. · If there is an ...
- What is Conditional Access in Azure Active Directory?
- Jun 22, 2023 — Conditional Access is Microsoft's Zero Trust policy engine taking signals from various sources into account when enforcing policy decisions.
- What are Azure Active Directory recommendations?
- Jul 12, 2023 — The Azure AD recommendations feature provides a holistic view into your tenant's security, health, and usage.
- Frequently asked questions about Azure Active Directory
- Common questions and answers about Azure and Azure Active Directory, password management, and application access.
- Azure Active Directory is Becoming Microsoft Entra ID
- Azure Active Directory (Azure AD) is becoming Microsoft Entra ID. Explore this cloud identity and access management solution that safeguards your data.
- Azure Active Directory SLA performance
- May 23, 2023 — Go to Azure AD, select Monitoring & health, then select Scenario Health from the side menu. Select the SLA Monitoring tab. Hover over the graph ...
Keywords
Microsoft Entra, Microsoft Azure AD, Tenant Authentication, Historical Authentication Availability, Backup Authentication, Active Directory