- All of Microsoft
Enhance Security with Entra Conditional Access Custom Auth
Customize Security: Enhance Microsoft Entra with Tailored Authentication Strengths
Key insights
Overview of Custom Authentication Strength in Microsoft Entra: This summary outlines the key insights regarding the implementation of custom Authentication Strength options within Microsoft Entra and their application in Conditional Access Policies. Authentication Strength controls in Conditional Access specify permissible combinations of authentication methods to access resources, enhancing security and flexibility.
Authentication Strength allows administrators to define what combinations of authentication methods can access a resource, increasing security for sensitive resources by requiring more robust authentication methods, like phishing-resistant options.
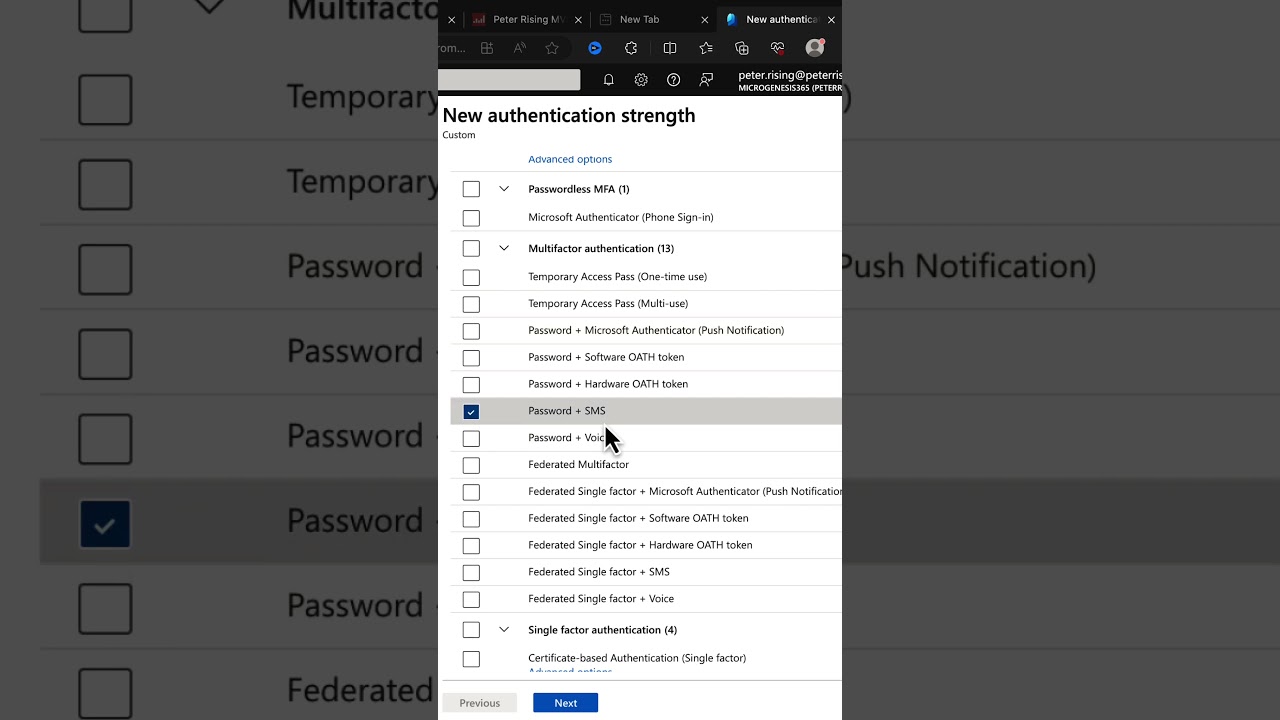
Administrators have the flexibility to create custom Authentication Strengths in addition to utilizing three built-in strengths provided by Microsoft: Multifactor Authentication, Passwordless MFA, and Phishing-Resistant MFA strength, to cater to various security needs.
Built-in authentication strengths consist of predefined combinations that can include, among others, Windows Hello for Business, FIDO2 security key, and Microsoft Entra certificate-based authentication (Multifactor), ensuring diverse and secure access options.
Conditional Access policies applying Authentication Strength are evaluated post initial authentication. Importantly, if a policy requires a phishing-resistant method, a user initially using a password must subsequently authenticate via a compliant method like a FIDO2 security key.
Authentication Strength cannot be used simultaneously with the 'Require multifactor authentication' control in the same Conditional Access policy, given built-in authentication strengths encompass multifactor authentication requirements.
More about Custom Authentication in Microsoft Entra
The introduction of custom Authentication Strength in Microsoft Entra represents a significant advancement in conditional access policies and enterprise security. It allows organizations to define and enforce authentication requirements tailored to the specific security needs of their resources, actions within applications, and access scenarios. This flexibility is critical in addressing the nuanced and evolving security landscape, particularly as organizations navigate challenges like sensitive resource access, user risk, and remote work.
By offering both built-in and customizable authentication strength options, Microsoft Entra empowers administrators to precisely control how resources are accessed based on the authentication methods deemed secure for various contexts. This includes requiring stronger authentication methods for high-risk users or when accessing resources from outside the corporate network, thus adding a critical layer of security.
Furthermore, the feature addresses scenarios involving guest user access and sensitive actions within applications, ensuring comprehensive coverage across user activities and access points. The ability to create custom strengths based on specific authentication method combinations allows organizations to adapt to new security threats efficiently, providing enduring and flexible solutions.
Despite the advantages, there are limitations, including the inability to restrict initial authentication and certain issues related to external users and unsupported authentication methods. Nevertheless, the overall impact of custom Authentication Strength in Microsoft Entra conditional access policies signifies a robust framework for securing access to organizational resources, enhancing both security and user experience in a cloud-centric world.
Learn how to create your own custom Authentication Strength options in Microsoft Entra and use them in your Conditional Access Policies. Microsoft Entra allows for the specification of combinations of authentication methods to access resources, adapting to varying security requirements. Users can meet these requirements through any permitted combination of authentication methods, enhancing flexibility and security.
Authentication strength is pivotal in Conditional Access, enabling administrators to define necessary authentication combinations for accessing sensitive or less sensitive resources. This capability is rooted in the Authentication methods policy, permitting the scoping of authentication methods for users and groups across federated applications in Microsoft Entra. Such configurations ensure tailored security measures based on factors like sensitivity of resources, user risk, and geographical location.
Utilizing authentication strengths addresses multiple scenarios, including requiring specific authentication methods for accessing sensitive resources or when actions within an application are deemed sensitive. It caters to the necessity for more secure authentication methods for high-risk users or guest users from other tenant resources. This flexibility underscores Microsoft Entra's commitment to versatile security controls.
Administrators have the power to determine an authentication strength when creating a Conditional Access policy through the Require authentication strength control. Options include built-in authentication strengths like Multifactor authentication strength, Passwordless MFA strength, and Phishing-resistant MFA strength, as well as custom-built strengths tailored to specific needs. This ensures that organizations can maintain robust security measures.
Built-in authentication strengths are predefined combinations provided by Microsoft, reflecting an ongoing commitment to update and enhance security as new methods become available. For example, the Phishing-resistant MFA strength entails methods such as Windows Hello for Business, FIDO2 security keys, or certificate-based authentication, all aimed at preventing phishing attempts and securing access to resources.
Various authentication method combinations satisfy different strengths, such as MFA strength for multifactor authentication requirements, and Passwordless or Phishing-resistant strengths for more advanced security needs. These include options like FIDO2 security keys, Microsoft Authenticator, and more, fostering a secure and flexible authentication ecosystem.
Conditional Access policies, however, are evaluated post-initial authentication, meaning users' first sign-in attempt isn't restricted by authentication strength. This necessitates the use of phishing-resistant methods for continued access if required by the policy. Such distinctions underscore the nuanced application of these strengths in real-world scenarios.
Microsoft Entra does not allow the simultaneous use of Require multifactor authentication and Require authentication strength in the same Conditional Access policy due to the redundancy in security requirements they represent. Certain authentication methods, like Email one-time pass for guest users, are not currently supported by authentication strength, highlighting ongoing development areas.
The Authentication strength relies on the Authentication methods policy, enhancing its scope by enabling further restrictions for specific scenarios. This tight integration between policies ensures a tailored and comprehensive approach to security, allowing administrators to configure authentication methods precisely for user groups or individual users, enhancing both security and flexibility.
To use Conditional Access and Authentication Strengths in Microsoft Entra, tenants require a Microsoft Entra ID P1 license. Proper user experience hinges on enabling combined MFA and SSPR registration, ensuring that registration processes align with required authentication methods, fostering a seamless and secure user experience.
Understanding Microsoft Entra Conditional Access and Authentication Strengths
Microsoft Entra plays a crucial role in modern cybersecurity, enhancing the flexibility and security of access control policies through Conditional Access and Authentication Strengths. By allowing administrators to specify exactly which combinations of authentication methods are required to access different resources, it aligns security measures with the specific needs and risks associated with those resources. This ensures that sensitive resources are only accessible via secure authentication methods, such as phishing-resistant options like FIDO2 security keys and Windows Hello for Business, thereby significantly reducing the risk of unauthorized access.
Moreover, the ability to create custom authentication strengths caters to the unique security requirements of each organization, allowing for a tailored approach to resource access. This flexibility is essential in addressing specific scenarios such as sensitive actions within applications, access by high-risk users, or even guest access across tenant resources. The seamless integration of Authentication Strengths with the Authentication methods policy underlines Microsoft Entra's commitment to providing a comprehensive and adaptable security framework that meets the evolving challenges of digital access and identity management.
Despite its vast capabilities, it's important to note that Conditional Access policies apply post-initial authentication, indicating that the selection of an appropriate authentication method is crucial only after the user's identity is initially verified. Furthermore, the development and integration of new authentication methods continue to enhance the security and usability of Microsoft Entra, ensuring that organizations can protect their resources effectively against emerging threats.
In summary, Microsoft Entra's Conditional Access and Authentication Strengths offer a powerful toolset for organizations to secure their digital assets. By allowing for precise control over the authentication processes, Microsoft Entra ensures that access to resources is both secure and adaptable to the specific needs of the organization, making it an essential component of modern identity and access management strategies.
Learn how to craft your own custom authentication strength options within Microsoft Entra and incorporate them into your Conditional Access Policies. This process allows for tailored security measures suited to varying access needs and scenarios. Whether it's bolstering defenses around sensitive resources or adjusting authentication methods based on user risk, location, and more, Microsoft Entra facilitates a more controlled and secure environment.
Administrators have the liberty to define authentication strengths through Conditional Access policies, which include built-in options like Multifactor Authentication, Passwordless MFA, and Phishing-resistant MFA. Additionally, creating custom strengths tailored to specific requirements is an option, providing further flexibility in security protocols. These strengths are built upon the foundation of the authentication methods policy, allowing administrators to designate certain authentication methods for specific user groups across Microsoft Entra ID federated applications.
Specific scenarios where authentication strengths can be invaluable include accessing sensitive resources, performing sensitive actions within an application, or accessing applications outside of a corporate network, especially for high-risk users or guest users from different tenants. It's worth noting, though, that Conditional Access policies catering to authentication strength are assessed post-initial authentication phase, which implies that although a user can log in using a password, they might need to authenticate through a more secure method like the FIDO2 security key to proceed.
Understanding the Microsoft Entra Authentication Strengths
Utilizing Microsoft Entra effectively requires comprehending how authentication strengths integrate with Conditional Access to enhance security. These strengths dictate the authentication method combinations permissible for accessing resources, thus enabling administrators to enforce security based on the level of sensitivity of the resource or the user's scenario. Built-in strengths offer predefined combinations by Microsoft, ensuring reliable security configurations that align with the latest authentication methods. Meanwhile, custom authentication strengths offer the flexibility to meet unique organizational needs, optimizing security and user experience.
Moreover, navigating through the intricacies of using Microsoft Entra necessitates familiarity with requirements such as the Microsoft Entra ID P1 license and the importance of enabling combined registration for MFA and SSPR. This foundational knowledge ensures that both administrators and users can leverage the full potential of Microsoft Entra's security features, thereby safeguarding sensitive information and applications from unauthorized access more effectively.

People also ask
What are the strengths of authentication methods?
Authentication strength functions as a Conditional Access control, delineating the acceptable combinations of authentication methods for resource access. By meeting the defined strength criteria through any sanctioned combination, users can gain the necessary authentication.
What is the limitation of Conditional Access policy?
A notable constraint within the Conditional Access framework is the cap of 195 policies for each tenant, defining the boundary for security policy implementation.
What is the best practice for Conditional Access policy for MFA?
For bolstering the security posture of your Microsoft 365 environment, it is advisable to implement nine pivotal conditional access policies. These include restricting logins to specific countries, blocking obsolete device operating systems, mandating compliant devices, requiring devices to be Hybrid Azure AD joined, instituting app protection policies, blocking users or sign-ins flagged as high risk, and enforcing Multi-Factor Authentication (MFA).
What is the difference between MFA and authentication strength?
Authentication strength in the realm of Conditional Access is a strategic control allowing for the specification of precise Multi-Factor Authentication (MFA) combinations required for external users to access organizational resources. This approach is particularly advantageous for limiting access to sensitive applications by external entities.
Keywords
Entra Conditional Access, Custom Authentication, Authentication Strengths, Access Policies, Security Policies, User Authentication, Policy Customization, Adaptive Access, Secure Authentication, Authentication Strategies