- All of Microsoft
Secure Power Automate HTTP Request by IP Address
Restrict HTTP Request in Power Automate by IP to secure your workflow and protect from unauthorized access.
Key insights
- This video explains how to secure the Power Automate trigger "When a HTTP Request is received" by restricting it to specific IP Addresses.
- By default, anyone with the flow URL can potentially execute the flow.
- Restricting access by IP can significantly enhance the security of your automation processes.
Securing HTTP Requests in Power Automate
Power Automate offers remarkable flexibility for creating automated flows, but with great power comes the need for enhanced security. In scenarios where HTTP requests are used to trigger flows, ensuring that only trusted networks can access the URL is crucial. By configuring IP address restrictions, you can prevent unauthorized execution of your flows. This practice is especially vital when handling sensitive data or performing critical operations. Learning to implement these restrictions not only safeguards your automations but also elevates your understanding and control over the platform. Overall, securing HTTP requests is a key step in maintaining robust digital processes.
This blog post summarizes a YouTube video by Paul Murana on the topic of securing HTTP requests in Power Automate. The video showcases how to restrict access to "When an HTTP Request is received" triggers by using trusted IP addresses. This ensures that only specified IP addresses can execute the flow, enhancing security and preventing unauthorized access.
In this summary, we will delve into three sections covering the concept, implementation, and best practices for securing flows using IP restrictions in Microsoft automation tools.
This is crucial for organizations that need to safeguard their automated processes from unapproved usage.
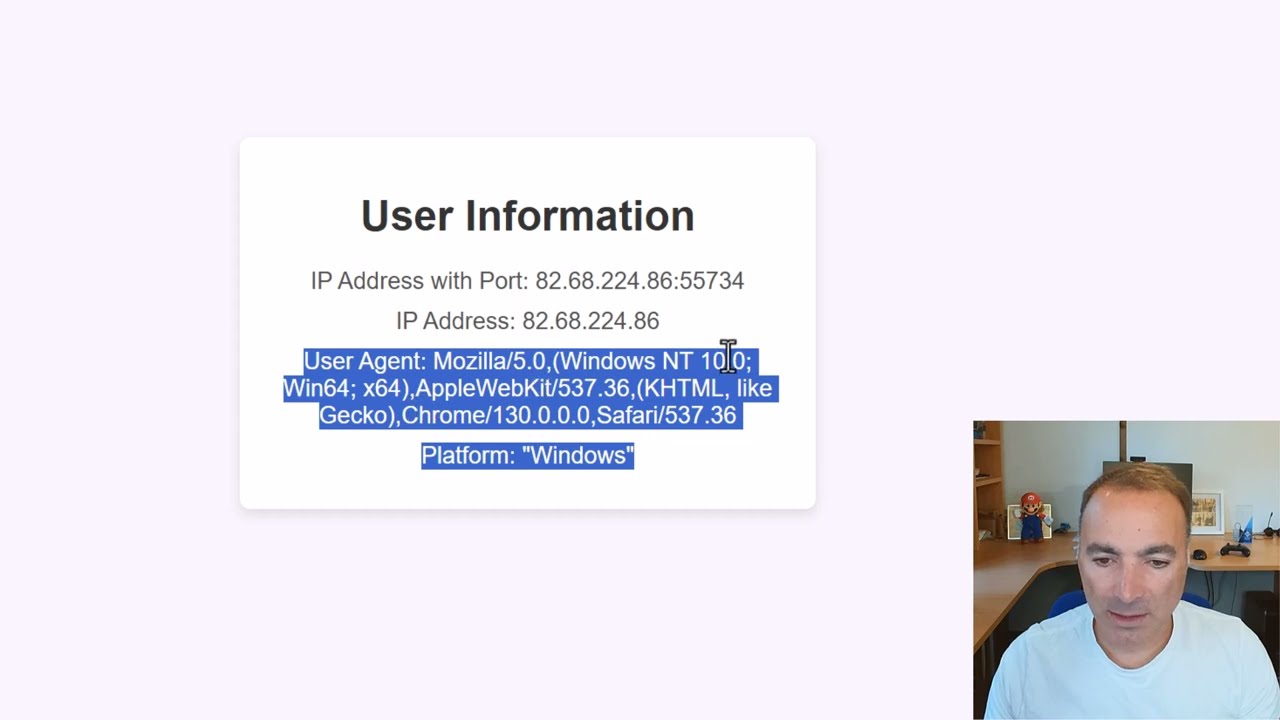
The video begins by explaining the importance of securing HTTP requests in Microsoft automation services. By default, flows triggered by an HTTP request can be executed by anyone with access to the flow URL.This presents a security risk for sensitive or critical processes.To mitigate this risk, IP restriction ensures that only requests coming from trusted IP addresses can trigger the flow. This additional layer of security is especially beneficial for businesses that manage confidential data or operations.
By implementing IP address filtering, the automation tools become better protected against unauthorized access.
Section 2: Implementing IP Address RestrictionsThe video tutorial provides a step-by-step demonstration on how to configure these IP restrictions within the automation software. Firstly, users need to define the trusted IP addresses that are allowed to access the flow.This involves editing the trigger settings to include specific conditional logic.Murana shows how to apply sample expressions to enable this functionality effectively.The process involves using conditional expressions which evaluate the source IP of incoming requests.
Exploring IP Restriction in Microsoft Automation
Securing HTTP requests within Microsoft automation services involves restricting trigger access to trusted IP addresses. This method significantly reduces the risk of unauthorized flow execution. By following a structured approach to implement IP filtering, organizations can safeguard their automated processes.
Key steps include defining trusted addresses, applying conditional logic in trigger settings, and maintaining an audit trail for monitoring purposes. Regular updates and understanding network implications are imperative for maintaining security efficacy. These measures, as demonstrated in Paul Murana's video, are essential for ensuring data and process integrity in today's digital landscape.

People also ask
"How to secure HTTP Request Power Automate?"
Securing your HTTP triggered flow in Power Automate involves implementing authentication measures to protect the endpoint from unauthorized access, typically using API keys or OAuth for secure connections. Thoroughly controlling who has access to these triggers enhances security.
"Is IP address included in HTTP Request?"
While the client IP address typically is not present directly in the HTTP headers, web servers have the ability to identify the IP address from the TCP connection that carries the HTTP request.
"How do I send a HTTP Request to Power Automate?"
To send an API request, such as POST, GET, PUT, or DELETE, you should utilize the Invoke web service action within Power Automate. Populate the service's URL and select the necessary HTTP method in the action's properties. Furthermore, you must specify the request and response content types, such as XML or JSON.
"When a HTTP Request is received, Power Automate anyone?"
You can use the "When an HTTP request is received" trigger in Power Automate to initiate workflows by receiving requests to the flow's specified endpoint. It's possible to limit who can initiate such workflows by ensuring that only authenticated users are permitted, enhancing the security of the process.
Keywords
Secure HTTP Request, Power Automate, IP Address, HTTP Request Security, Power Automate Guide, Automate IP Filtering, HTTP Automation Tips, Secure Workflow Automation