- All of Microsoft
Optimize Security: Microsoft Cyber Architecture
Explore Microsofts Cybersecurity Reference Architectures for a secure, Zero Trust strategy across platforms and apps.
Key insights
Understanding the Microsoft Cybersecurity Reference Architectures is crucial for any organization aiming to establish a comprehensive cybersecurity strategy based on Zero Trust principles. The Microsoft Cybersecurity Reference Architectures (MCRA) is part of Microsoft's Security Adoption Framework (SAF) and outlines integration of cybersecurity capabilities across multiple Microsoft and third-party platforms such as Microsoft 365, Microsoft Azure, ServiceNow, Salesforce, AWS, and GCP.
The December 2023 update of the MCRA provides key insights into antipatterns (common mistakes), best practices, guiding rulesets for architecture, as well as mapping Microsoft's capabilities to organizational roles and Zero Trust standards. In addition, it addresses securing privileged access, reference plans in SAF, and prioritizing based on attacker return on investment (ROI).
To utilize the MCRA effectively, it can serve as a starting template for security architecture, a comparison reference to review existing security capabilities, or as a comprehensive learning tool for understanding Microsoft's extensive cybersecurity capabilities and their integration within the security ecosystem.
- Deep dive into Microsoft’s cybersecurity capabilities and technologies.
- Comprehensive insight into best practices and common mistakes.
- Guidance on implementing a Zero Trust architecture.
- Facilitation of security technology comparison and learning.
- Understanding the integration of Microsoft’s cybersecurity investments.
Exploring Cybersecurity with Microsoft
The field of cybersecurity is ever-evolving, with new threats emerging and technologies advancing to counteract them. Microsoft plays a critical role in this landscape by providing a suite of security solutions designed to protect organizations across various environments—from in-house servers and clouds to mobile devices and operational technology. Emphasizing the importance of the Zero Trust model, which trusts nothing and verifies everything, Microsoft is at the forefront of encouraging robust security strategies among its users.
Leveraging tools like the Microsoft Cybersecurity Reference Architectures, professionals can gain valuable insights into avoiding common pitfalls and embracing best practices that fortify their security posture. This framework acts not just as a resource for setting up security systems, but also as a learning mechanism to understand the intricate nature of cybersecurity and the role Microsoft's tools play within it. Therefore, staying informed about the latest Microsoft cybersecurity guidelines and integrations is not only beneficial but essential for anyone tasked with safeguarding IT infrastructures and data in today's complex digital world.
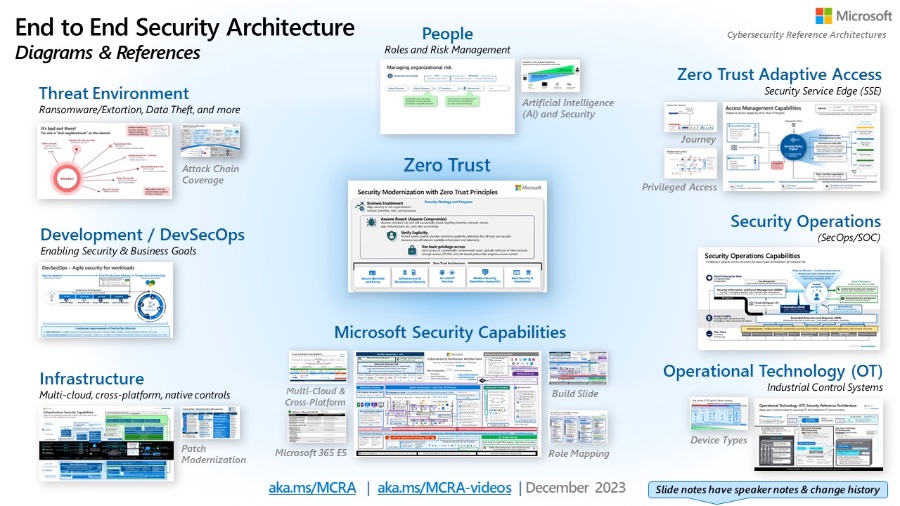
Understanding the Microsoft Cybersecurity Reference Architectures is crucial for firm's aiming to ensure their systems are secured based on Zero Trust principles. In the informative video hosted by Peter Rising, a thorough examination of these architectures is provided. Recognized as an essential resource, they are part of Microsoft's Security Adoption Framework (SAF) that details various cybersecurity capabilities and technologies.
The Microsoft Cybersecurity Reference Architectures (MCRA) include both Microsoft products and third parties'. They involve integrations with platforms such as Microsoft 365, Azure, ServiceNow, Salesforce, AWS, and GCP, as well as AI functionalities. This shows the comprehensive coverage these architectures provide across a diverse range of technologies and platforms.
Some key features of the MCRA include identification of common security missteps, a set of guiding principles, and a deep dive into threat and attack patterns. They also provide mappings of Microsoft's capabilities according to organizational roles and Zero Trust standards, advice on securing privileged access, and recommendations on cybersecurity investment prioritization.
The collection additionally presents detailed technical diagrams, which are instrumental for understanding various aspects necessary for a robust cybersecurity strategy. These diagrams cover Microsoft's own security capabilities, operational protocols, multicloud and cross-platform capabilities, and much more. It's a significant compilation for anyone responsible for or interested in security operations.
To effectively utilize the MCRA, viewers can treat it as a starting point for building a security architecture, especially since it covers a broad range of modern enterprise needs, including mobile and IoT. It's likewise useful for comparing existing security infrastructure with Microsoft's recommendations. This helps organizations recognize what they already have and what they might be missing.
Moreover, the MCRA serves as an educational resource, providing ScreenTips and links for further reading. It's beneficial for those learning about Microsoft's suite of security capabilities and how they might be integrated with current systems. Lastly, aspiring cybersecurity professionals, or those considering a career shift, will find value in this rich source of informational content as they build foundational knowledge.
- Antipatterns (common mistakes) and best practices
- Guiding rulesets for end to end architecture
- Threat trends, and attack patterns
- Mapping Microsoft capabilities to organizational roles
- Mapping Microsoft capabilities to Zero Trust standards
- Securing privileged access
- Reference plans in SAF (including example of patching modernization)
- Prioritizing using attacker return on investment (ROI)
The video does not only guide through Microsoft's security blueprints but also sheds light on the broader landscape of digital security practice trends. It's valuable for those interested in the latest frameworks and technologies shaping the cybersecurity industry. As Microsoft continues to expand its offerings, professionals can utilize resources like the MCRA to help navigate the multifaceted world of cybersecurity.
Microsoft Cybersecurity Reference Architecture Video
Introduction to the Microsoft Cybersecurity Reference Architectures:
This video provides a detailed walkthrough of the Microsoft Cybersecurity Reference Architectures. It's a crucial resource for organizations aiming to develop their protection strategy aligning with Zero Trust principles.
What the MCRA encompasses:
The Microsoft Cybersecurity Reference Architectures are a part of Microsoft's Security Adoption Framework, illustrating Microsoft's protective capabilities and integration potential with both Microsoft and third-party technologies.
Integration of Microsoft Security:
These architectures describe the functionality of security within the context of Microsoft's ecosystem and illustrate how they can be applied in conjuction with third-party services and platforms.
- Microsoft 365 and Microsoft Azure
- Third-party apps like ServiceNow and Salesforce
- Third-party platforms such as AWS and Google Cloud Platform
- Both first and third-party AI capabilities
Contents of the MCRA:
The Microsoft Cybersecurity Reference Architectures provide a treasure trove of knowledge, from recognizing common missteps to outlining comprehensive best practice guidelines.
- Threat trends and patterns
- Mappings of Microsoft's capabilities to organizational roles
- Mappings to Zero Trust frameworks
- Measures for securing privileged access
- Sample plans within the Security Adoption Framework, such as patching modernization strategies
- Approaches for prioritizing based on attacker ROI
Detailed Diagrams:
A variety of technical diagrams are included that demonstrate the depth and breadth of Microsoft's security capabilities.
- Illustrations of security capabilities
- Zero trust user access
- Security operations
- Operation technology security
- Multicloud and cross-platform capabilities
- Attack chain coverage
- Infrastructure and Development Security
- Security organizational functions
Utilization of the MCRA:
The video details several ways the MCRA can serve professionals and organizations.
- As a starting template for security architecture planning
- For comparing existing security capabilities with Microsoft's recommendations
- To learn about Microsoft's security technologies and integration efforts
- As an educational resource for those new to the field
Read the full article Understanding the Microsoft Cybersecurity Reference Architectures!

Keywords
Microsoft Cybersecurity Reference Architectures, Cybersecurity Best Practices, Microsoft Security Solutions, Cybersecurity Frameworks, Security Reference Models, Enterprise Security Architecture, Secure Microsoft Environments, Cyber Threat Protection, Microsoft Security Technologies, Advanced Threat Defense.
