Learn White Hat Hacking with Power Automate 2024
Master White Hat Hacking in Power Automate: Unlock Secure Data Access & Identify Vulnerabilities
Key insights
- Introduction to Power Automate hacking emphasizes enjoying the process of problem-solving and exploring vulnerabilities in the system.
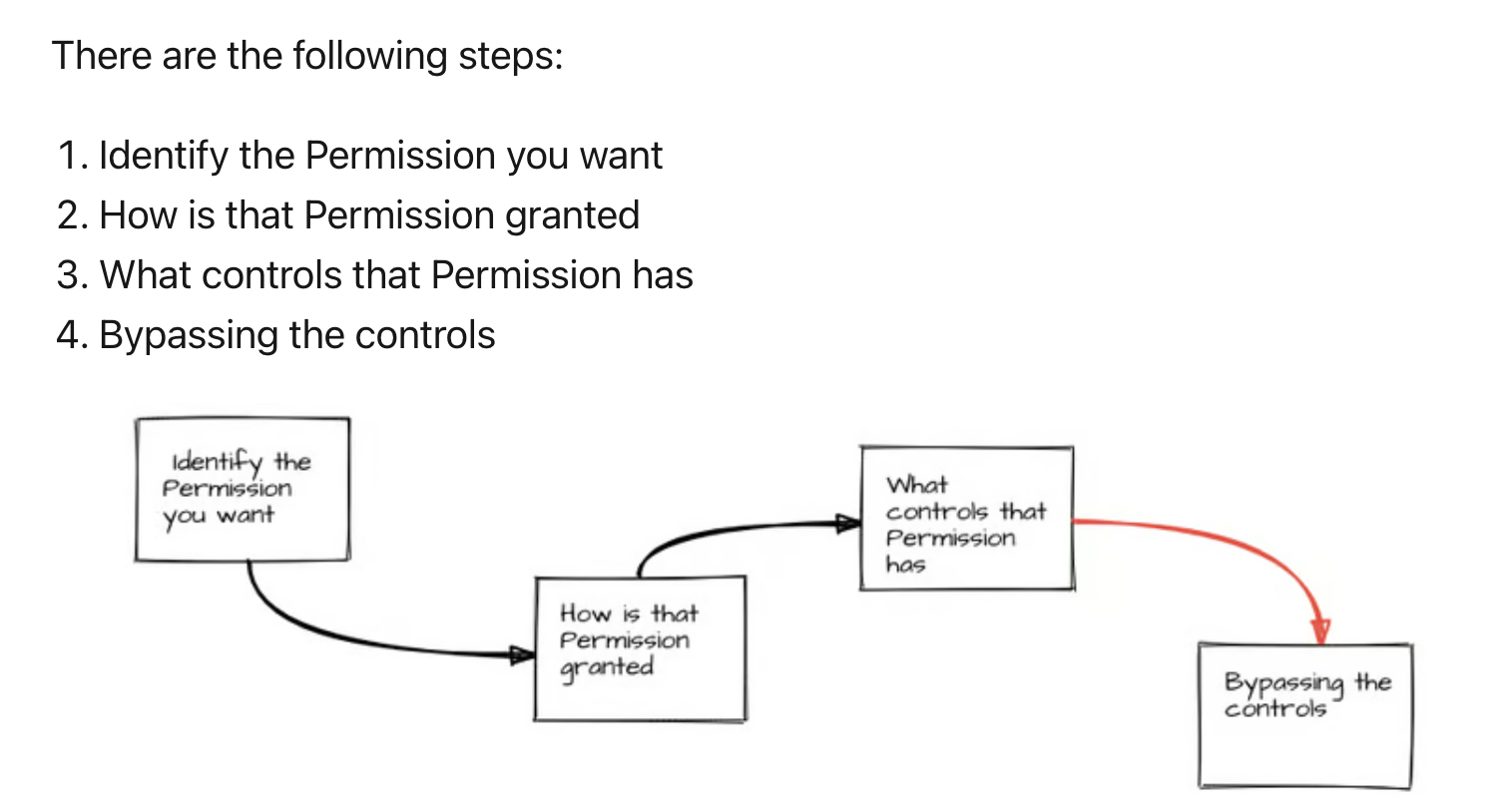
- Steps to identify and manipulate permissions include identifying the desired permission, understanding how it is granted, and exploring ways to bypass controls associated with these permissions.
- David Wyatt (MVP) delves into technical methods using Postman and browser developer tools to exploit and test limitations within Power Automate's permission and connection systems.
- Despite rigorous attempts, the trials to manipulate and create unauthorized connections for malicious purposes were unsuccessful, showcasing the robust security measures deployed by Microsoft.
- The process offers significant learning opportunities, helping in both understanding the platform's internal works and enhancing general development practices.
Exploring White Hat Hacking in Power Automate
In the realm of digital security, white hat hacking serves as a constructive approach, allowing users to test systems like Power Automate for vulnerabilities. This blog post by enthusiast David Wyatt walks readers through the systematic approach he employs to unveil and understand potential security loopholes. Focusing on connections within the Power Platform, Wyatt elaborates on how permissions are manipulated. Despite the complexity of Power Automate's systems, his attempts to exploit and bypass controls are thwarted due to rigorous security measures by Microsoft, highlighting their commitment to tight security protocols. This narrates not only the challenge involved in such ethical hacking attempts but also the potential learning derived from each trial, which inadvertently fortifies developers' competencies in building more robust applications.
Read the full article How to be a White Hat Hacker in Power Automate
![]()
In an insightful blog about white hat hacking within Power Automate, the author shares their experiences and methodologies for identifying vulnerabilities in the Power Platform. Despite their deep understanding and strategic approach, they found that Microsoft had already addressed potential security issues, showcasing the robustness of the platform's security measures.
The writer outlines a step-by-step process starting with identifying the desired permissions and exploring how they can be accessed or granted through connection sharing in flows. This process reveals various permissions an attacker might target such as reading emails, accessing secure data, or manipulating flow logs and apps.
A critical part of their exploration includes attempting to bypass controls which are well-guarded in Microsoft's ecosystem. They discuss the Principle of Least Privilege (PoLP) and Defence in Depth, two key security principles that are sometimes overlooked in practice, leaving potential vulnerabilities.
Further experiments involved using API tools like Postman and Browser Dev Tools to manipulate and access connections through illicit means. However, despite their extensive efforts to exploit these supposed vulnerabilities, the established security measures thwarted every attempt, illustrating the challenges and complexities of ethical hacking.
The ethical hacker’s journey, while unsuccessful in breaching the platform's defenses, serves as an invaluable exercise in understanding and fortifying digital environments. Such efforts highlight the importance of continuous security scrutiny and improvement, which not only ensures the safety of platforms but also enhances the skills and knowledge of the developers and security experts involved.
Understanding Ethical Hacking in Automated Platforms
The art of ethical hacking involves meticulously testing and probing a system to discover potential security vulnerabilities that malicious hackers could exploit. In the realm of Power Automate and wider automated platforms, this practice is crucial for fortifying security measures. Ethical hackers use various tools and methods, including API manipulation and permission testing, to simulate potential attacks. The insights gained from these activities are pivotal in tightening security protocols and ensuring that the platforms remain secure against unauthorized access and data breaches. Through this proactive approach, organizations can safeguard their operations, protect sensitive information, and maintain trust with their users.
People also ask
What is the professional name for a white hat hacker?
White hat hackers, also known widely as ethical hackers or good hackers, represent the opposite of black hat hackers. They deliberately breach computer systems or networks with the goal of uncovering security vulnerabilities that can then be addressed and rectified, enhancing the system's security integrity.
Are grey hat hackers legal?
While grey hat hackers often operate with positive intentions, their activities can lead them to face legal repercussions. Engaging in unauthorized access, even for potentially beneficial outcomes, places them in a conflicting position with law enforcement and governmental bodies, raising questions about the ethics of their actions.
Keywords
white hat hacker Power Automate, ethical hacking Power Automate, learn white hat hacking Power Automate, Power Automate security, become a white hat hacker, cybersecurity Power Automate, ethical hacker training Power Automate, Power Automate hacking techniques