Active Directory Access with Microsoft Entra Private Access
Unlock Active Directory access anywhere with Microsoft Entra Private Access integration and conditional security.
Key insights
- Use Microsoft Entra Private Access for secure access to AD-trusted resources regardless of their location, integrating conditional access protections.
- Configure firewalls for Active Directory domains ensuring specific ports are open for required services like LDAP, RPC, and DNS among others.
- Dynamic client port ranges have changed in Windows Server 2008 and later versions to comply with IANA recommendations, affecting configurations in firewalls.
- Active Directory utilizes ICMP ping for verifying server availability during prolonged LDAP requests to prevent time-outs.
- DNS servers in Windows Server environments may use a specific registry setting to change their client-side port querying behavior, enhancing security and efficiency.
Understanding Microsoft Entra Private Access and Active Directory Configuration
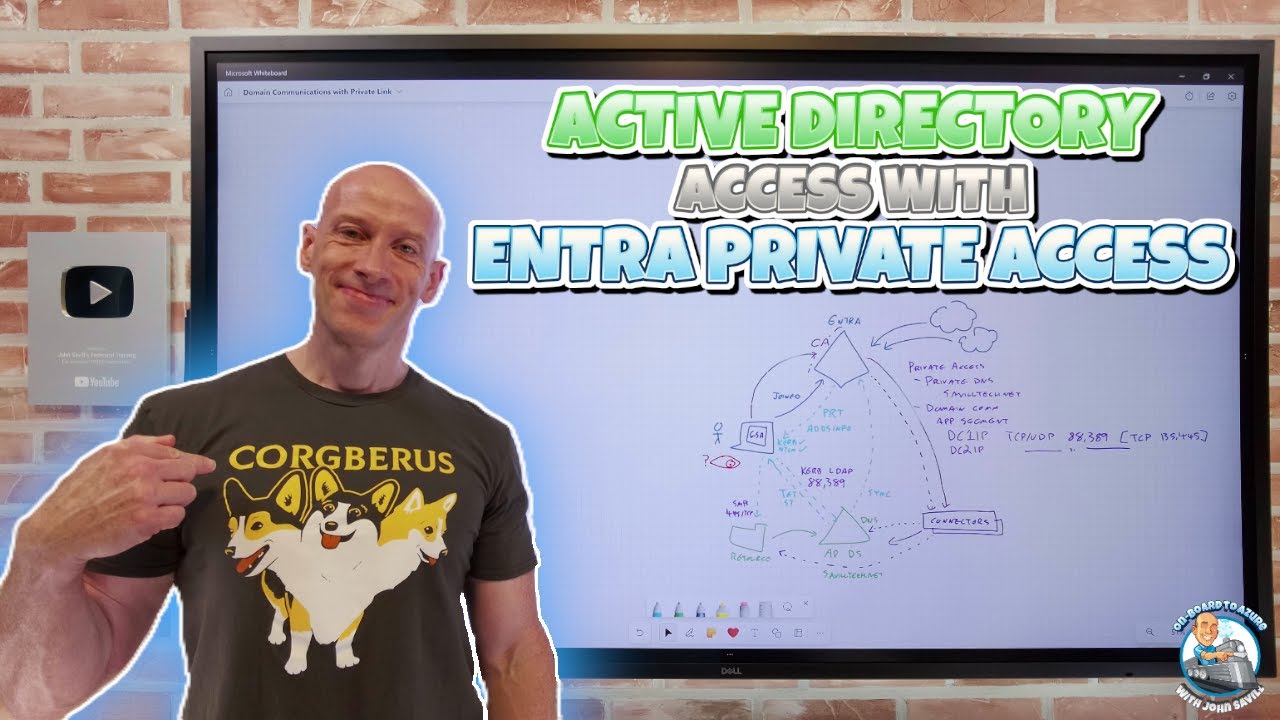
Active Directory Access with Microsoft Entra Private Access allows communication with AD-trusted resources from any location. This solution integrates the benefits of conditional access among other security measures. The process encompasses a step-by-step guide including resource access, DNS configuration, and the importance of certain ports for effective communication.
The discussion also spans technical requirements for Microsoft Entra Private Access, insights into DNS experiences, and details on configuring private access for Active Directory. Furthermore, the article elaborates on the configuration process within Entra, viewing tickets, and enhancing communication flow through adding conditional access.
Moreover, it covers firewall configuration for Active Directory domains and trusts applicable to various Windows Server versions, highlighting the significance of understanding port requirements for different scenarios. Special attention is given to the dynamic port range change for Windows Server 2008 and newer, emphasizing compliance with IANA recommendations.
- Introduction to Microsoft Entra Private Access and AD-trusted resource access.
- Details on DNS configuration and essential ports for secure communication.
- Guide on configuring Private Access for Active Directory and enhancing security.
- Firewall setup for Active Directory domains across multiple Windows Server versions.
- Emphasis on dynamic port range adjustments for improved server communication.
Active Directory plays a crucial role in network security and resource access control within a Windows Server environment. It outlines the use of client and server ports necessary for various services including RPC, LDAP, and more. Additionally, the article mentions ICMP's role in ensuring server availability, further enhancing network reliability.
PPTP tunneling protocol and its requirements are also discussed, alongside insights on enabling GRE protocol. These configurations aid in securing and optimizing network communications. The article concludes with a caution against direct port information usage for configuring Windows Firewall, suggesting a more comprehensive approach for network setup.
Read the full article Active Directory Access with Microsoft Entra Private Access

People also ask
What is Microsoft Entra private access?
Microsoft Entra Private Access facilitates the designation of fully qualified domain names (FQDNs) and IP addresses deemed private or internal by an organization, enabling control over how these resources are accessed.
Is Azure Active Directory now Microsoft Entra ID?
Azure Active Directory has been rebranded as Microsoft Entra ID. This change, announced on June 20, 2023, sees the continuation of the same capabilities and service level agreements previously known under Azure AD.
Which two services are provided by Microsoft Entra?
Within the Microsoft Entra suite of identity and access capabilities, two key services include authentication and single sign-on (SSO). Authentication ensures the verification of a user or device’s identity.
Why did Microsoft change Azure to Entra?
The transition to Microsoft Entra ID marks an advancement and consolidation within the Microsoft Entra product family, highlighting the company’s dedication to streamlining secure access experiences. All attributes and functions of Azure AD remain accessible under Microsoft Entra ID.
Keywords
Active Directory Access, Microsoft Entra Private Access, Zero Trust Security, Remote Access Solutions, Entra Private Connectivity, Secure Network Access, Identity and Access Management, AD Integration Best Practices